What Happens to Your Data After a Phishing Attack?

The click has happened.
The form is filled out.
The data is sent.
So what now?
First stop: The dark web
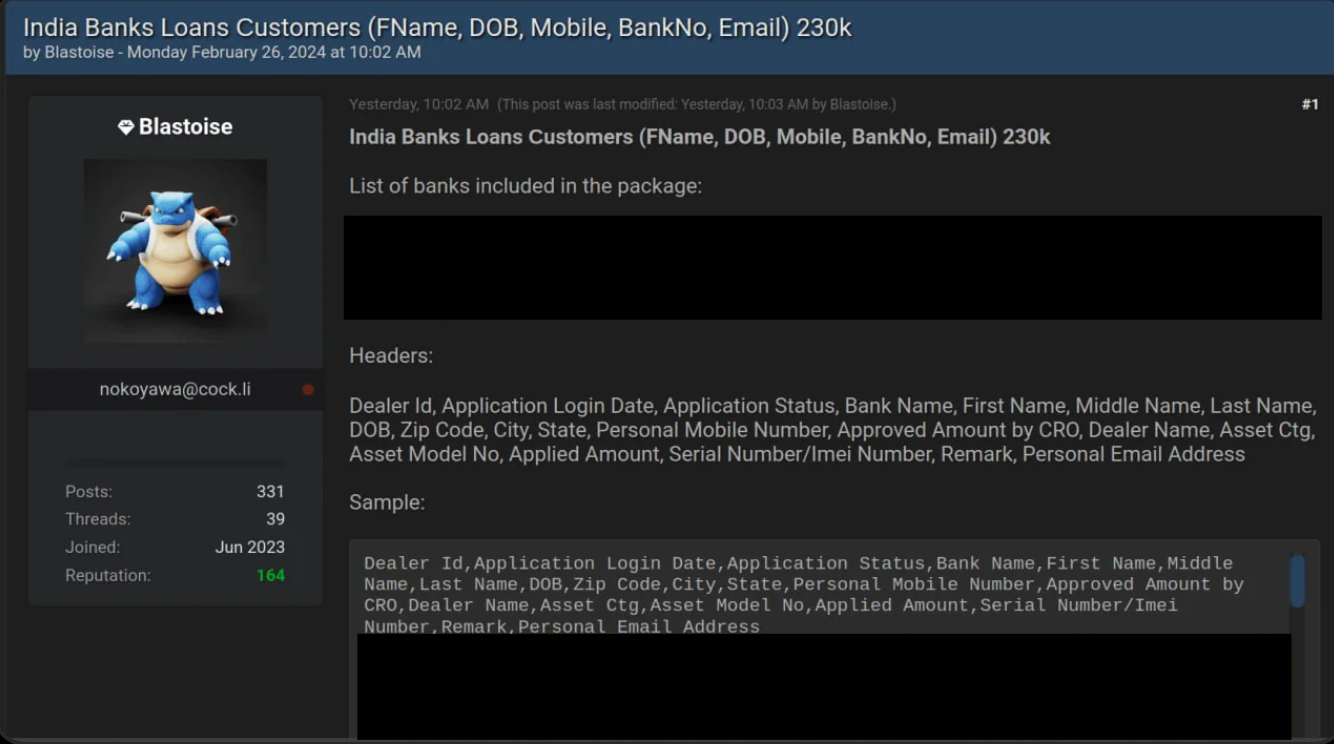
After a phishing attack, your stolen information isn’t always exploited immediately. Instead, your information disappears into systems built for one purpose only: to turn your information into profit.
The data is immediately sent to the attackers via one of three methods:
- Email - less common today, as it’s easy to block
- Telegram bots - extremely popular, attackers receive data in real time
- Admin panels - specialized software that automatically sorts and verifies stolen information
Within seconds of clicking “Log in”, your data is already on the move. Attackers gain immediate access to what you entered, often enough to connect you to email accounts, online services, or payment platforms.
In many cases, attackers don’t use the data themselves.
Instead, they sell it, because it’s easier and far more profitable.
From Phishing to Profit: How It Works
A typical chain looks like this:
- Data is collected via phishing – you enter your information
- Hackers sell the data on dark web marketplaces – often in bulk, cheaply
- Criminal “data analysts” buy and verify it – testing credentials, enriching profiles
- Resale to specialized buyers – for fraud, extortion, or identity theft
The Price of Your Data: How Little It Cost To Buy You
It's shockingly cheap to buy access to someone's digital life. Here's what you're actually worth on the market:
| Type of data / account | Price (NOK) | Price (USD, approx.) |
|---|---|---|
| Netflix & Spotify accounts | As low as 10 kr | $1 |
| Credit card details | 30-350 kr | $3 - $35 |
| Email credentials (f.eks. Gmail) | 50-400 kr | $5 - $40 |
| Stolen PayPal accounts | 110-1 200 kr (Depending on balance) | $11 - $120 |
| Passport scans or ID copies | 150-1 000 kr (Depending on country) | $15 - $100 |
| Full identity package | Around 1 500kr | $150 |
| Banking access | 700–20 000 kr (avg 3 500 kr) | $70 - $2,000 |
| Crypto exchange accounts | 600–4 000 kr (avg 1 050 kr) | $60 - $400 |
Prices vary based on factors such as:
- Is two-factor authentication enabled?
- Is a payment card linked?
- How old and “trusted” is the account?
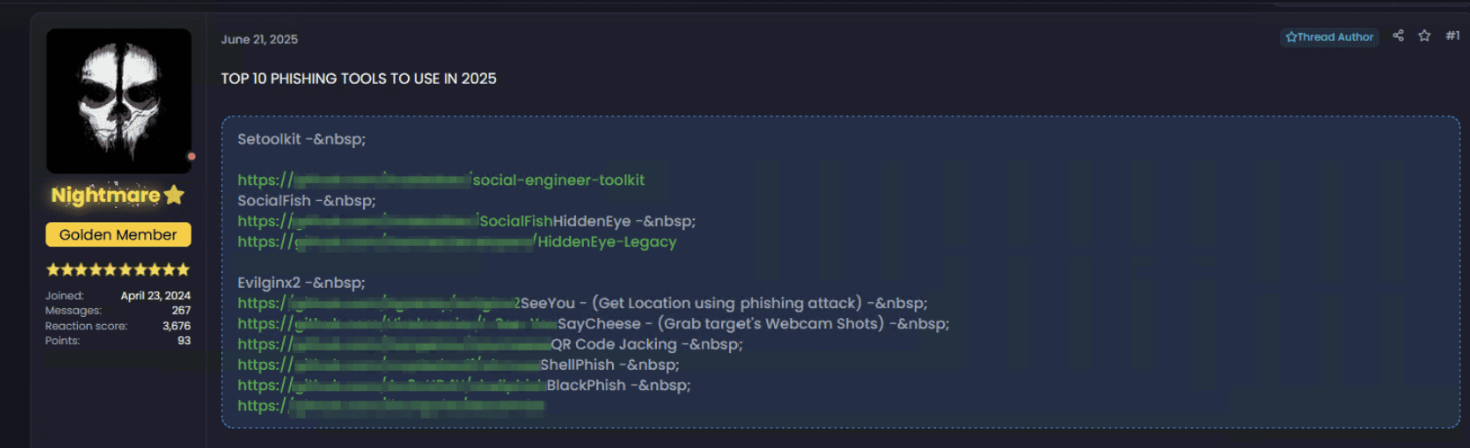
Sorting And Verification
Before your data reaches its highest value, it goes through a process.
First, it lands in massive databases containing information from thousands, or millions of victims. These datasets are sold cheaply in bulk on dark web forums or Telegram channels because the buyer has to do the hard work themselves: sorting, testing, and verifying what actually works.
The buyers of this data aren't your typical hackers, they're "data-analysts" working within criminal networks. Their job is to:
- Clean the data – remove duplicates and invalid entries
- Verify – test whether credentials actually work
- Enrich – combine it with data from previous breaches to build a full profile of you
- Categorize – sort by value: bank customer? social media user? crypto holder?
Today, much of this trade doesn’t even happen exclusively on the dark web, it happens openly in Telegram channels, where stolen data is shared, sold, and exchanged in real time.
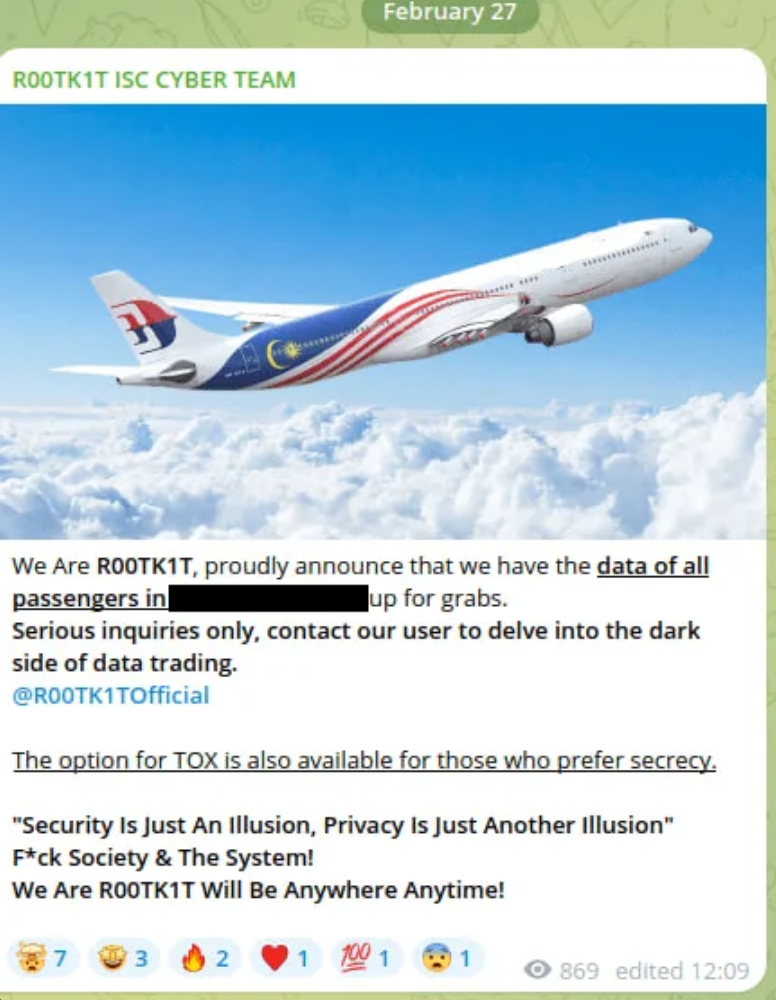
How Your Data Is Used In Practice
So what do buyers actually do with your information? Here are some real scenarios:
1. Financial fraud
With access to cards, accounts, and email, criminals can drain accounts, purchase goods, or transfer money in your name. They know your address, so they may ship items to a nearby location and collect them themselves.
2. Account takeover
When someone has access to your email, they can reset passwords on everything from social media to banking, and gain full control. They log into your social media accounts, download all the pictures, and use them to deceive others, or create deepfakes.
3. Identity theft
Using your personal details, criminals can create fake accounts, apply for loans, or build an entirely new criminal identity in your name. With your documents, they can open accounts, order goods, or take out credit.
4. Extortion and sextortion
Do you have sensitive files, messages, or photos stored in your accounts? These can be used to blackmail you for money.
(Important: most extortion emails are pure scare-tactics, it’s rare that attackers actually have what they claim.)
5. Long-term social engineering
Some don't do anything at all, not right away. They just monitor, gather more data, and use it later to target you, or someone you work with.
Concrete example:
The attacker knows you work in the finance department at a company (from LinkedIn). They send an email that appears to come from the managing director: "Hi, can you transfer 100,000 kr to this supplier? It's urgent!" The email looks real because they've hacked the boss's email account by using the same password that was stolen six months ago.
The frightening part? This can happen months or even years after the original phishing attack. Your data sits in databases, waiting to be used.
What You Can Do – Before And After An Attack
Before you’re targeted:
- Activate two-factor authentication on everything you can – use an authenticator app (try to avoid SMS, one-time codes via SMS can be intercepted)
- Use unique passwords, preferably with a password manager – it's impossible to remember strong, unique passwords for 50+ accounts
- Be critical! Even emails that look real can be spoofed
- Don't click on links or open attachments you don't trust 100%
- Check the URL: Before you log in, look carefully at the domain name. Is it "bankennorge.com" or "banken-norge.com"? The small difference is everything

After an attack:
- Change passwords immediately – on all accounts where you used the same password
- Block cards and contact the bank if you provided payment info
- Report the phishing attempt to email provider or website
- Check if your email has been leaked: www.haveibeenpwned.com
- Check active sessions: Go into all important accounts and log out all logged-in devices you don't recognize
- Keep software updated: Old browsers and operating systems have known vulnerabilities that phishing tools exploit
Summary: Where Does Your Data Go After Phishing?
A phishing attack is the start of a criminal supply chain. Your data is sold on the dark web for anything from a few kroner to thousands. It can be abused for financial fraud, account takeover, extortion, and identity theft.
The most important thing is that we understand how this actually works.
When we know what phishing is, how data is misused, and how fast it happens, we’re far better equipped to protect ourselves. Knowledge makes us more aware, more critical, and less vulnerable.
Phishing isn’t just about technology, it’s about people.
And the more we know, the harder we are to deceive.


